欧国联积分榜_亚洲区世预赛积分榜

*** 达到当天最大量:500000,请联系开发者***
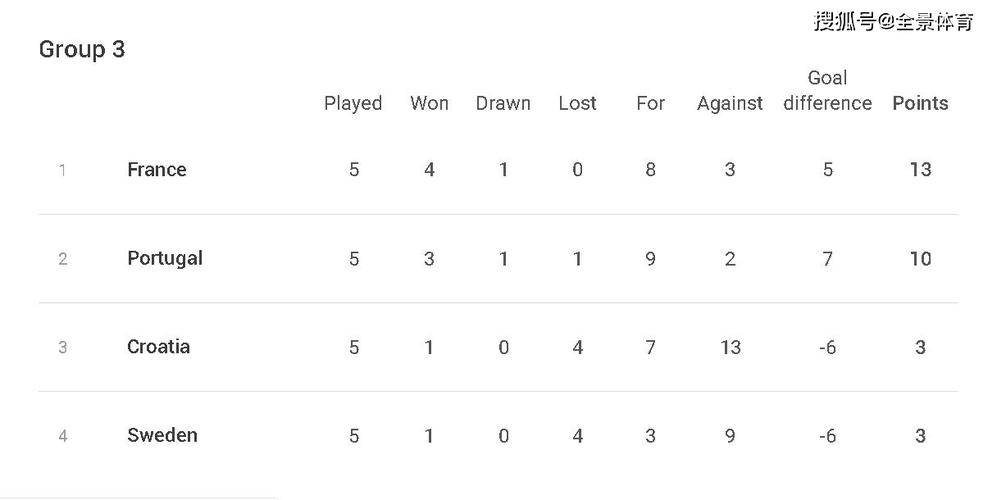
2022-2023赛季欧国联小组赛最新积分榜排名如下: A级A组: 1、丹麦,3胜0平1负,积分9; 2、克罗地亚,2胜1平1负,积分7; 3、奥地利,1胜1平2吩咐,积分4; 4、法国,0胜2平2负,积分2; ...欧国联全称“欧洲国家联赛”,由欧洲足球协会联盟主办。欧国联参赛者为欧洲成年国家队,且每两年举行一届。为了方便广大球迷们观看欧国联赛事,球天下体育为大家准备了完整的欧国联赛...
欧洲国家联赛D是欧洲国家联赛的第四级别(最低级别)比赛,参赛的队伍是欧国联成绩在第49-55位(即最后7位)的国家队。7支球队分成2个小组,一组3个队,一组4个队,进行主客场双循环...欧国联最新积分榜 这一轮的焦点战一定是英德大战,英格兰的世界排名(第5名)和身价虽然要强于德国队(第12名),但德国人不怵英格兰人,而且已经有超过半个世纪的时间,英格兰从未...
德国队继续保持不败,可是也连续三场不胜,以致积分并不高,暂列小组第三。英格兰队此前不敌匈牙利,近期的2场又连续平局,以致目前仅积2分,排名C组垫底位置。 D组:本组荷兰队的表现强势,前三轮2胜1平...排名小组第一;英格兰1胜1平,进1球失0球,净胜1球,积3分,小组排名第二;丹麦1平1负,进0球,失2球,净胜-2球,积1分,小组排名第三;冰岛两负,进1球失6球,净胜-5球,积0分,小...
+△+ 500彩票网为您提供2022-2023赛季欧国联赛程积分榜、欧国联赛程赛果等相关的数据,包含欧国联2022-2023赛季的联赛赛制、比赛时间、主客队比分、比赛结果、主场、客场、近6场、上半场、下半场等详细...第一小组中,荷兰1-0战胜波兰,荷兰净胜1球积3分,排小组第一,波兰净胜-1球积0分,小组垫底,意大利1-1战平波黑,两队净胜球都为0,各积1分,暂并列小组第二;第二小组中,比利时、...
≥^≤ 500彩票网为您提供2023/2024赛季女欧国联积分榜、女欧国联助攻榜、女欧国联数据统计、女欧国联赛程等相关的数据资料,包含赛果分布情况、进球分布情况、胜平负...欧国联A级最新积分榜:克罗地亚荷兰晋级,法国输球仅排小组第3 北京时间9月26日凌晨,欧国联最后一轮小组赛比赛展开争夺。在A级的几场焦点之战当中,丹麦队在主场迎战法国队,奥地利队主场面对克...



